Hands-on Project 4-3
What is DNS ?
" It refers to Domain Name System (DNS). It is a hierarchical naming system for computers, services, or any resource connected to the internet or a private network. It associates various information with domain names assigned to each of the participants.
Most importantly, it translate domain names which are meaningful to humans into numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide. "
Click here for source
------------------------------------------------------------------------------------
Homepage of website (www.course.com)

Right click on notepad and run as administrator

Navigate to C:\windows\system32\drivers\etc and select "hosts"

Type in the IP address for Google and the website that you want to direct from

After saving the file, go to www.course.com
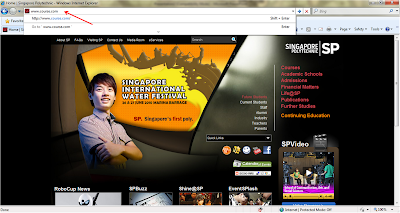
The original website is now directed to Google.com

-----------------------------------------------------------------------------------
Reflection
Attackers can make use of the local hosts file and alter the user's most frequent website to another IP address, where by the website contains virus that is harmful to your computer. If they succeeded in planting virus like keylogger into your computer, then your personal information like passwords or credit card numbers will be captured down and transmitted back to the attacker without the user's acknowledgement.
And of course, the attacker wouldn't only target one user only, so there will also be countless of users out there affected by the same problem.















































