Hands-on Project 11-3
Homepage of TrueCrypt, click on the highlighted link
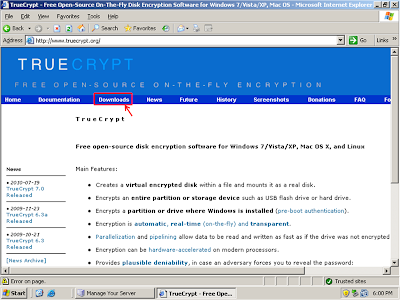
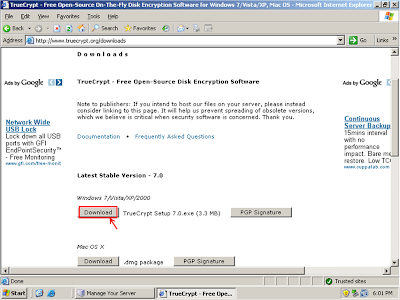
Click 'Download' under Windows 7/Vista/XP/2000
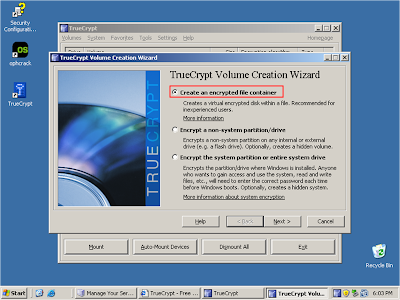
Select 'Create an encrypted file container'
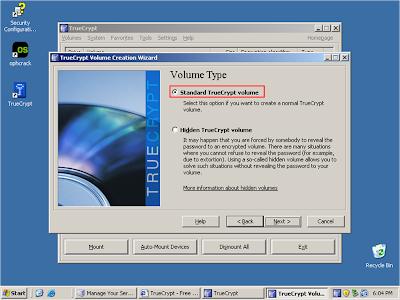
Select 'Standard TrueCrypt volume'
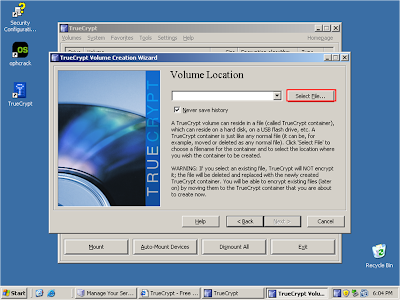
Click 'Select File'
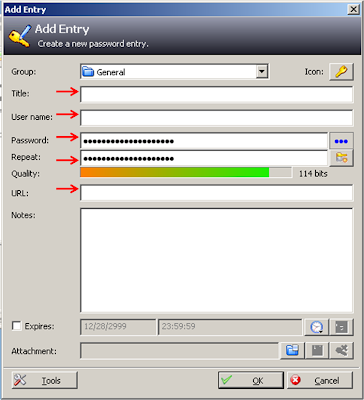
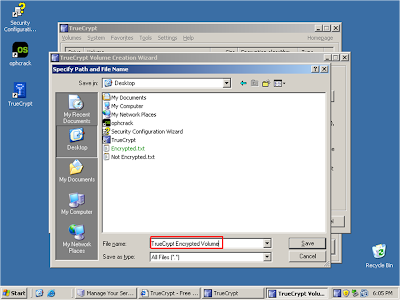
Name the volume as "TrueCrypt Encrypted Volume"
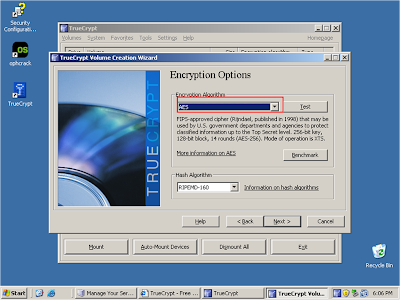
Ensure that AES is selected
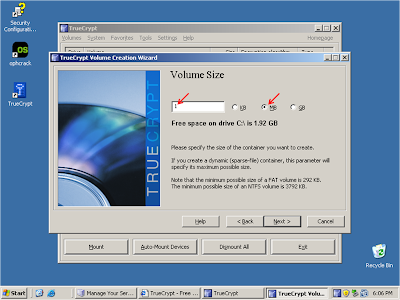
Type "1" in the textbox then select "MB"
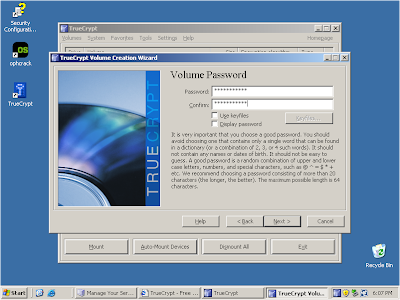
Enter password in the textbox provided
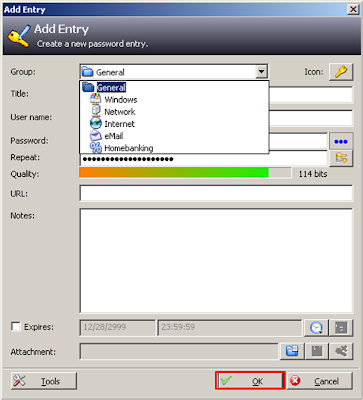
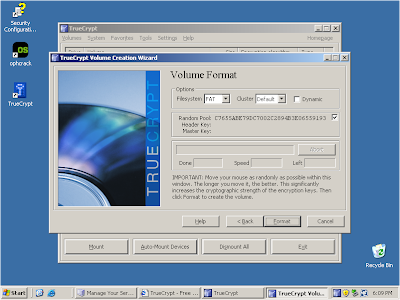
Click 'Format' to continue
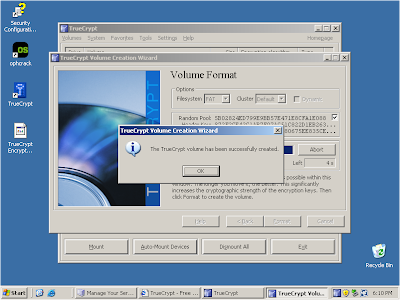
Click 'OK' to finish creating the volume
========================================
Reflection
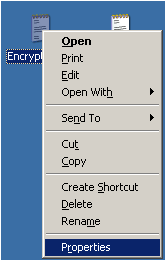
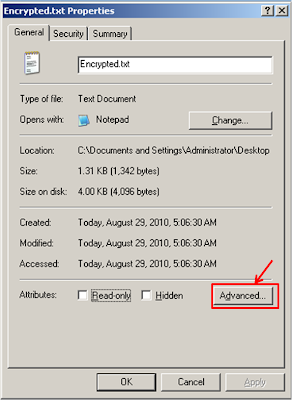
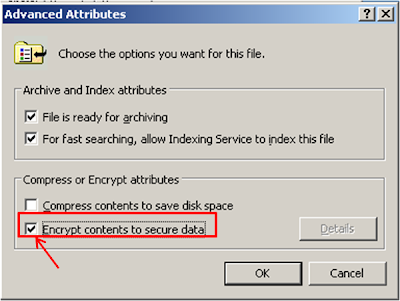
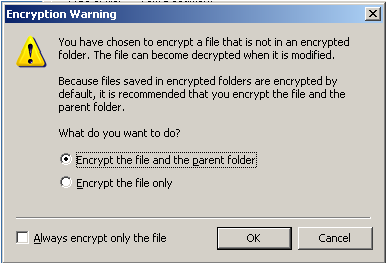
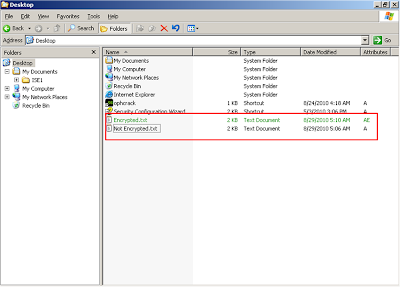
I think that EFS is more convenient to use as we do not have to download a extra program to just a encrypt a file or folder and all we need to do is just to edit the properties of the file or folder that we want to encrypt.
But because of the fact that not all Windows OS supports the encrypting function, so TrueCrypt will come in handy for those user whose computer doesn't support encrypting function.