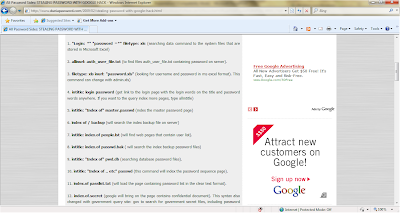
Hands-on Project 1-3
Homepage of Secunia

List of programs covered

Screenshots while doing the scan


------------------------------------------------------------------------------------------------
Reflecion
As many software vendors does not have the function of being able to notify the user of the security updates each month, this causes a lot of applications to remain unpatch. Hence increasing the number of malware present in our computer.
Being users ourselves, in order to keep our computers secure, we need to use online software scanner like Secunia, to detect the unpatch applications in our computer and provide us with the instructions to fix the certain application. Therefore this decreases the chances of our computer crashing due to these unpatch applications.